
4/16 CHANNEL DVR
User Manual

4/16 CHANNEL DVR
User Manual
4/16 Channel DVR
User Manual
Copyright
??2014 Samsung Techwin Co., Ltd. All rights reserved.
Trademark



 is the registered logo of Samsung Techwin Co., Ltd.
is the registered logo of Samsung Techwin Co., Ltd.
The name of this product is the registered trademark of Samsung Techwin Co., Ltd.
Other trademarks mentioned in this manual are the registered trademark of their respective company.
Restriction
Samsung Techwin Co., Ltd shall reserve the copyright of this document. Under no circumstances, this document shall be reproduced, distributed or changed, partially or wholly, without formal authorization of Samsung Techwin.
Disclaimer
Samsung Techwin makes the best to verify the integrity and correctness of the contents in this document, but no formal guarantee shall be provided. Use of this document and the subsequent results shall be entirely on the user's own responsibility. Samsung Techwin reserves the right to change the contents of this document without prior notice.
????Design and specifications are subject to change without prior notice.
????The initial administrator ID is ???admin??? and the password should be set when logging in for the first time.
Set password for your wireless network if you use the product with a wireless router. Being not protected with password or using the default wireless router password may expose your video data to potential threat.
Please change your password every three months to safely protect personal information and to prevent the damage of the information theft.
Please, take note that it???s a user???s responsibility for the security and any other problems caused by mismanaging a password.

overview
Important Safety Instructions
Read these operating instructions carefully before using the unit.
Follow all the safety instructions listed below.
Keep these operating instructions handy for future reference.
1)Read these instructions.
2)Keep these instructions.
3)Heed all warnings.
4)Follow all instructions.
5)Do not use this apparatus near water.
6)Clean only with dry cloth.
7)Do not block any ventilation openings, Install in accordance with the manufacturer???s instructions.
8)Do not install near any heat sources such as radiators, heat registers, stoves, or other apparatus (including amplifiers) that produce heat.
9)Do not defeat the safety purpose of the polarized or grounding- type plug. A polarized plug has two blades with one wider than the other. A grounding type plug has two blades and a third grounding prong. The wide blade or the third prong are provided for your safety. If the provided plug does not fit into your outlet, consult an electrician for replacement of the obsolete outlet.
10)Protect the power cord from being walked on or pinched particularly at plugs, convenience receptacles, and the point where they exit from the apparatus.
11)Only use attachments/accessories specified by the manufacturer.
12)Use only with the cart, stand, tripod, bracket, or table specified by the manufacturer, or sold with the apparatus. When a cart is used, use caution when moving the cart/apparatus combination to avoid injury from
13)Unplug this apparatus during lightning storms or when unused for long periods  of time.
of time.
14)Refer all servicing to qualified service personnel. Servicing is required when the  apparatus has been damaged in any way, such as
apparatus has been damaged in any way, such as
damaged, liquid has been spilled or objects have fallen into the apparatus, the apparatus has been exposed to rain or moisture, does not operate normally, or has been dropped.
overview!
English _3
overview
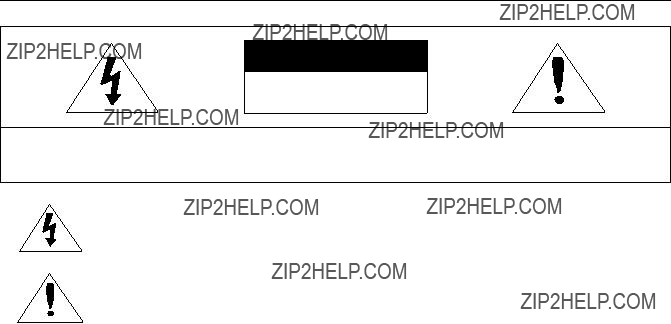
CAUTION
RISK OF ELECTRIC SHOCK.
DO NOT OPEN
CAUTION : TO REDUCE THE RISK OF ELECTRIC SHOCK, DO NOT REMOVE COVER (OR BACK) NO USER
SERVICEABLE PARTS INSIDE. REFER SERVICING TO QUALIFIED SERVICE PERSONNEL.
This symbol indicates that dangerous voltage consisting a risk of electric shock is present within this unit.
This exclamation point symbol is intended to alert the user to the presence of important operating and maintenance (servicing) instructions in the literature accompanying the appliance.
WARNING
???To reduce the risk of fire or electric shock, do not expose this appliance to rain or moisture.
???To prevent injury, this apparatus must be securely attached to the floor/wall in accordance with the installation instructions.
WARNING
1. Be sure to use only the standard adapter that is specified in the specification sheet. Using any other adapter could cause fire, electrical shock, or damage to the product.
2. Incorrectly connecting the power supply or replacing battery may cause explosion, fire, electric shock, or damage to the product.
3. Securely plug the power cord into the power receptacle. Insecure connection may cause fire.
4. When installing the camera, fasten it securely and firmly. The fall of camera may cause personal injury.
5. Do not place conductive objects (e.g. screwdrivers, coins, metal parts, etc.) or containers filled with water on top of the camera. Doing so may cause personal injury due to fire, electric shock, or falling objects.
6. Do not install the unit in humid, dusty, or sooty locations. Doing so may cause fire or electric shock.
7. If any unusual smells or smoke come from the unit, stop using the product. In such case, immediately disconnect the power source and contact the service center. Continued use in such a condition may cause fire or electric shock.
8. If this product fails to operate normally, contact the nearest service center. Never disassemble or modify this product in any way. (SAMSUNG is not liable for problems caused by unauthorized modifications or attempted repair.)
9. When cleaning, do not spray water directly onto parts of the product. Doing so may cause fire or electric shock.
10. Do not expose the product to the direct airflow from an air conditioner.
Otherwise, it may cause moisture condensation inside the Clear Dome due to temperature difference between internal and external of the dome camera.
11.If you install this product in a
Otherwise, external high, humid air may flow inside the housing, pooling moisture or vapor inside the product due to a difference between internal and external temperature.
4_ overview

Before Start
This user manual provides Information for using the DVR such as brief introduction, part names, functions, connection to other equipment, menu setup, etc.
You have to keep in mind the following notices :
??? SAMSUNG retains the copyright on this manual.
??? This manual cannot be copied without SAMSUNG???s prior written approval.
??? We are not liable for any or all losses to the product incurred by your use of
??? Prior to opening the case, please consult a qualified technician first. Whenever this is needed power must be removed from the unit.
??? Before installing an additional HDD or connecting an external storage device (USB HDD) to this DVR, check the compatibility. Consult your provider for the compatibility list.
Warning
??????Battery
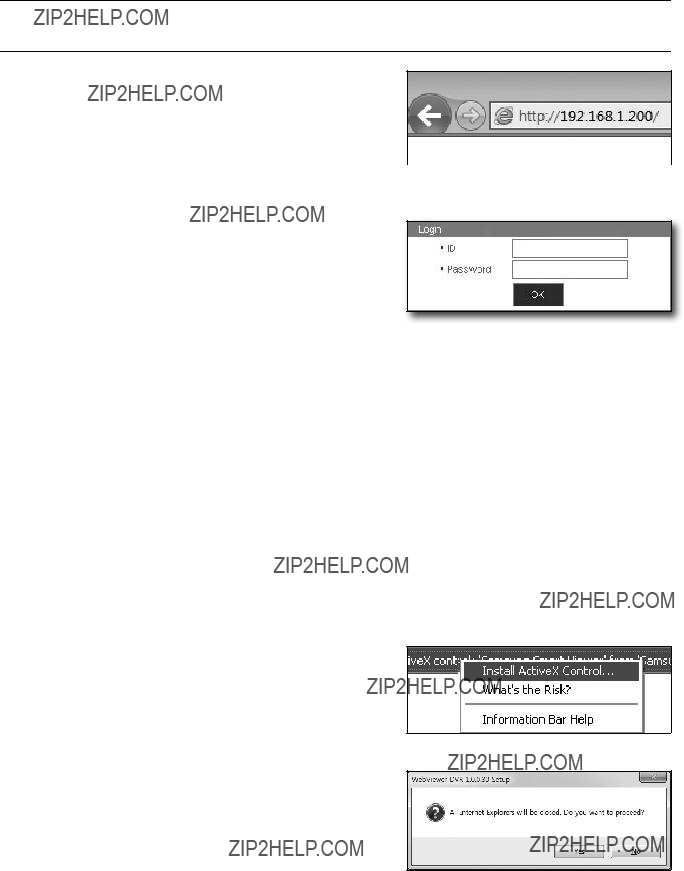
It is essential that when changing the battery in the unit, the replacement battery must be of the same type otherwise there may be a possibility of an explosion.
The following are the specifications of the battery you are using now.
??? Normal voltage : 3V
??? Normal capacity : 170mAh
??? Continuous standard load : 0.2mA
??? Operating temperature :
Caution
???Connect the power cord into a grounded outlet.
???The Mains plug is used as a disconnect device and shall stay readily operable at any time.
???Batteries shall not be exposed to excessive heat such as sunshine, fire or the like
???Risk of Explosion if Battery is replaced by an Incorrect Type. Dispose of Used Batteries According to the Instructions.
??????System Shutdown
Turning off the power while the product is in operation, or undertaking improper actions may cause damage or malfunction to the hard drive or the product.
Please turn off the power, please
You may want to install a UPS system for safe operation in order to prevent damage caused by an unexpected power stoppage. (Any questions concerning UPS, consult your UPS retailer.)
??????Operating Temperature
The guaranteed operating temperature range of this product is 0??C ~ 40??C (32??F ~ 104??F).
This product may not work properly if you run right after a long period of storage at a temperature below the guaranteed one.
Prior to using a device that has been stored for a long period in low temperatures, allow the product to stand at room temperature for a period.
Especially for the
??????Ethernet Port
DVR is designed for indoor use only and all the communication wirings are limited to inside of the building.
overview!
English _5

overview
Contents
connecting with other device
14
14 installation
14 Checking the Installation Environment
15 Connecting External Devices
15 Connecting the USB
15 Connecting External SATA HDD
16 Connecting the Camera
18 Connecting the
18 Connecting the Network
live
20
main menu
32
20 Getting Started
22 Live Screen Configuration
27 Live Mode
30 Zoom
30 Audio On/Off
30 Freeze
31 Event Monitoring
32 System Setup
44 Setting the Device
53 Setting the Recording
56 Setting the Event
58 Backup
60 Network Configuration
73 Controlling a PTZ Device
6_ overview
overview!
English _7

overview
Features
The DVR employs H.264 video encoding for 4/16 channel inputs and G.711 audio encoding for 4/16 channels while simultaneously supports hard disc recording and playback.
These DVRs also supports network connectivity, providing remote monitoring from a remote PC transferring video and audio data.
???Provides a convenient User Interface
???4/16 CH Composite Input Connectors
???Supports 720p/WD1/4CIF/2CIF/CIF recording formats
???With the network specific codec, network transfer enabled regardless of the recording conditions
???
???Display of HDD information and status by using HDD SMART
???Hard Disk overwrite function
???Mass storage hard disk backup through
???Simultaneous Record and Playback of
???Various Search Modes (Search by Time, Event, Backup and Motion Detection)
???Various Recording Modes (Manual, Event, Scheduled Recording)
???Remote Monitoring function by Network Viewer, Smart Viewer and Mobile Viewer
Standards Approvals
MM`` This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment.
This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the interference at his own expense.
8_ overview

package Contents
Please unwrap the product, and place the product on a flat place or in the place to be installed. Please check the following contents are included in addition to the main unit.
REC NETWORK POWER
overvIeW!
English _9

overview
pArT nAmeS And funCTIonS (fronT)
Sdr- C5300
Sdr- B3300
a
REC NETWORK POWER
c b
M ` All functions are operable with mouse control, since there are no front buttons.
10_ overview
An
c
English _11
overview
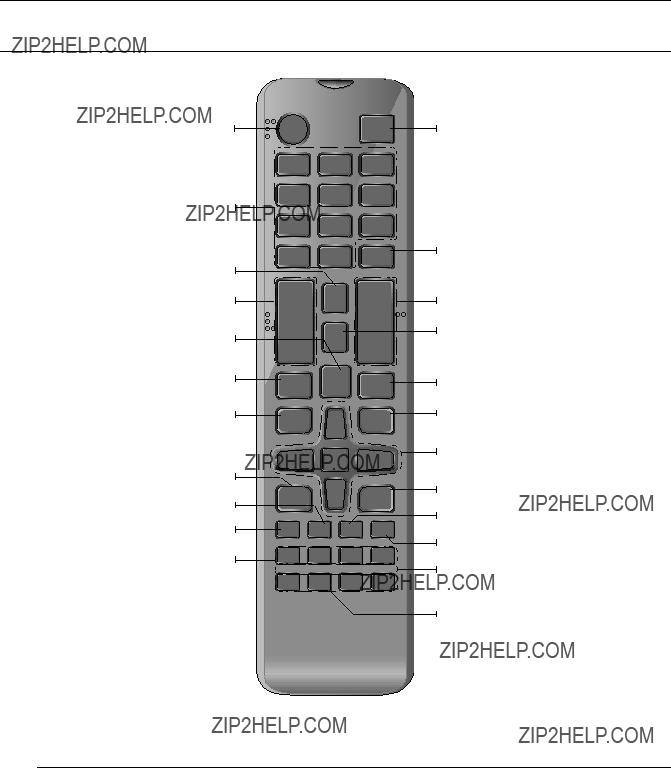
Remote Control
Using the numeric buttons
12_ overview

Changing the Remote Control ID
1.Press the [ID] button of the remote control and check the ID displayed on the DVR screen. The factory default ID of the remote control is 00.
2.Enter 2 digits of your selection in order, while pressing the system [ID] button.
3.When ID input is done, press the system [ID] button again to check the setting.
MM`` If you want to change the remote control ID to 08: Press 0 and 8 in order while the system [ID] button is pressed. Remote control's ID and DVR???s ID should be matched for proper operation. Refer to ???Remote Devices???. (Page 50)
overview!
English _13

connecting with other device
InSTALLATIon
Please take note of the followings before using this product.
???Do not use the product outdoor.
???Do not spill water or liquid in the connection part of the product.
???Do not impose the system to excessive shock or force.
???Do not pull out the power plug forcefully.
???Do not disassemble the product on your own.
???Do not exceed the rated input/output range.
???Use a certified power cord only.
???For the product with an input ground, use a grounded power plug.
CheCKInG The InSTALLATIon envIronmenT
Samsung Digital Video Recorder (???DVR??? hereinafter) is a state- Temperature
When the temperature rises inside the product, the product may breakdown and the product life be shortened. Please pay attention to the following recommendations before installation.
One Year: 24HR X 365 DAY =8,760 HR
The followings are the recommendations when Samsung DVR is installed on a rack.
1.Please ensure that the rack inside is not sealed.
2.Please ensure the air is circulated through the inlet/outlet as shown in the picture.
3.If the DVR or other devices on a rack is to be stacked as in the picture, provide a suitable space or install a ventilating opening for air circulation.
4.For natural air convection, place the inlet at the bottom of the rack and the outlet on top.
5.It is strongly recommended that a fan motor is installed at the inlet and the outlet for air circulation. (Please fit a filter at the inlet to screen dust or foreign substances.)
6.Please maintain the temperature inside the rack or surrounding areas between 0??C ~ 40??C (32??F ~ 104??F) as shown in the figure 1.
[Figure 1]
Life (Unit: HOURS)
[Figure 1]
D) Circuit Overloading - Consideration should be given to the connection of the equipment to the supply circuit and the effect that overloading of the circuits might have on overcurrent protection and supply wiring. Appropriate consideration of equipment nameplate ratings should be used when addressing this concern.
E) Reliable Earthing - Reliable earthing of
14_ connecting with other device

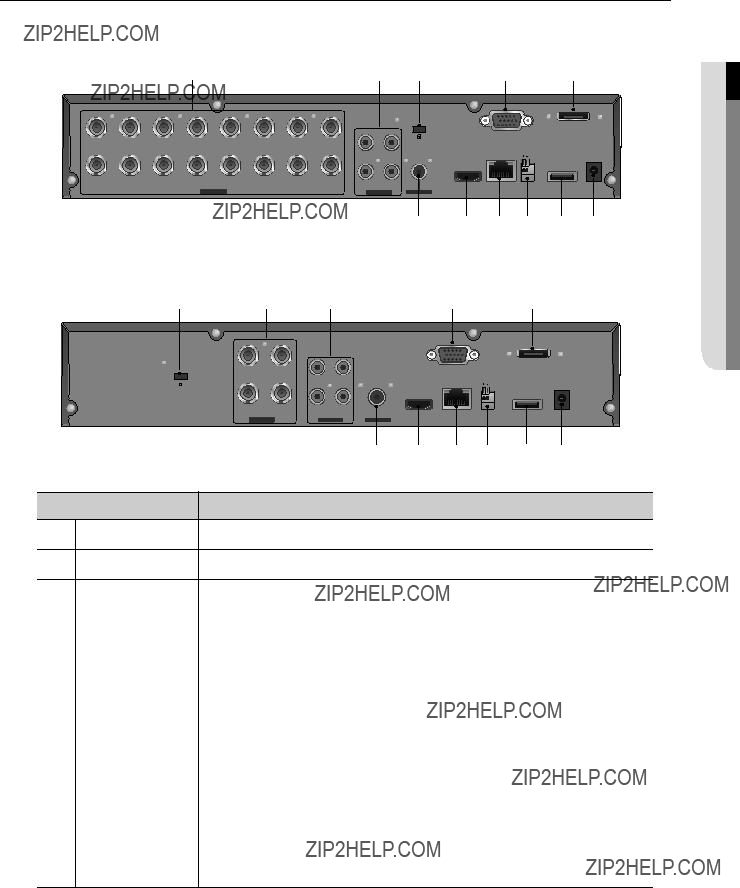
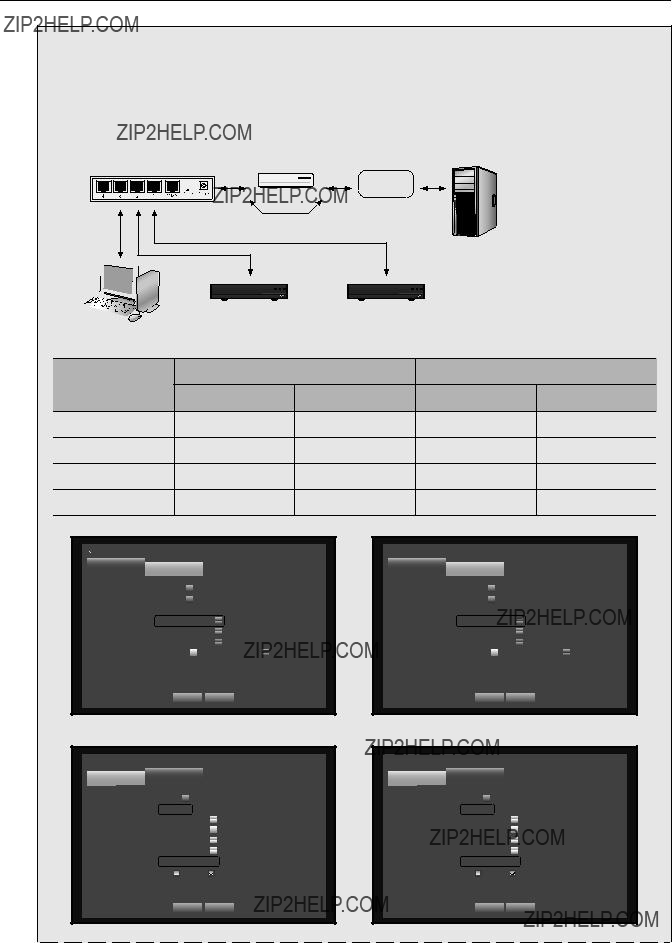
ConneCTInG exTernAL devICeS
` The following figures are based on Model
devICe oTher WITh ConneCTInG!
ConneCTInG The uSB
1.By factory default, a USB port is provided for external connection.
2.You can connect a USB HDD, USB memory or mouse to the USB port.
3.If a USB HDD is connected to the system, recognition and settings are available in ???main menu > Setting the device > Storage device???. (Page 47)
4.This product supports
J ` If you use the USB device for Backup purposes, format it with FAT32 on PC if it is not formatted on the DVR.
ConneCTInG exTernAL SATA hdd (eSATA)
` In the event of replacing an HDD of an external SATA HDD, please power off the external SATA HDD to change the HDD.
English _15

connecting with other device
ConneCTInG The CAmerA
Equipped with the IR LED and the illumination sensor, enables you to monitor at night as well as in daytime. The camera is suitable for both internal and external use.
`Please make sure not to fully expose the camera to rain. The camera must be installed under a shelter to avoid exposure to excessive rain or moisture.
a
b
c
d e
16_ connecting with other device

Connecting with dvr
` The following figures are based on Model
Installing the camera
The camera can be installed on the wall, ceiling, shelf or a desired position using the provided bracket.
devICe oTher WITh ConneCTInG!
wall or ceiling
1.Choose an installation site that can sufficiently support the weight of the equipments to be installed.
2.Attach the camera bracket to the wall using the supplied screws.
3.Adjust the direction of the camera to the desired direction, and fix bracket.
4.Fix the camera.
5.Connect the camera cable to the camera.
English _17

connecting with other device
ConneCTInG The
Connect the rear
ConneCTInG The neTWorK
` The following figures are based on Model
Connecting to network through ethernet (10/100BaseT)
VIDEO IN
Windows
Network Viewer
Hub/Switcher
NETWORK
18_ connecting with other device

Connecting to the Network using the router
other with connecting!
xDSL or Cable Modem

 xDSL or Cable Modem
xDSL or Cable Modem
device
DDNS Server
(Data Center)
Connecting to Network through ADSL
NETWORK
English _19

live
GeTTInG STArTed
Starting the system
1. Connect the power cable of the DVR to the wall outlet.
M ` Itbooting.takes about 10 seconds to display the start screen after
2.You will see the initialization screen.
The initialization process will last about 1 minute.
If a new HDD is installed, the initialization process may take longer.
REC
Shutting down the System
You can shut down the system only if you have logged in to the DVR.
You require permission to shut down the system if you are not logged in as admin.
20_ live

Login
LIve!
2.Click <Login>.
The login dialog appears.
You can also see the login dialog to access a desired menu by pressing the [menu] button on the remote control.
`The login dialog will also appear if you press a menu button on the remote control when the corresponding menu requires logging in.
`After logged in, press [RETURN] on the remote control to display the logout dialog.
Login
Locking All Buttons
This will restrict access to all buttons available in the DVR.
1.In Live mode, press buttons on the remote control in the order of [STop (@)]???[freeZe]???[STop (@)]???[freeZe]??? [menu].
All buttons will be locked.
2.In the lock condition, press any button to display a dialog where you are prompted to enter the password for unlocking the buttons.
The button lock will be released if you enter the admin password.
Key Lock Password
??? Password
OK Cancel
English _21

live
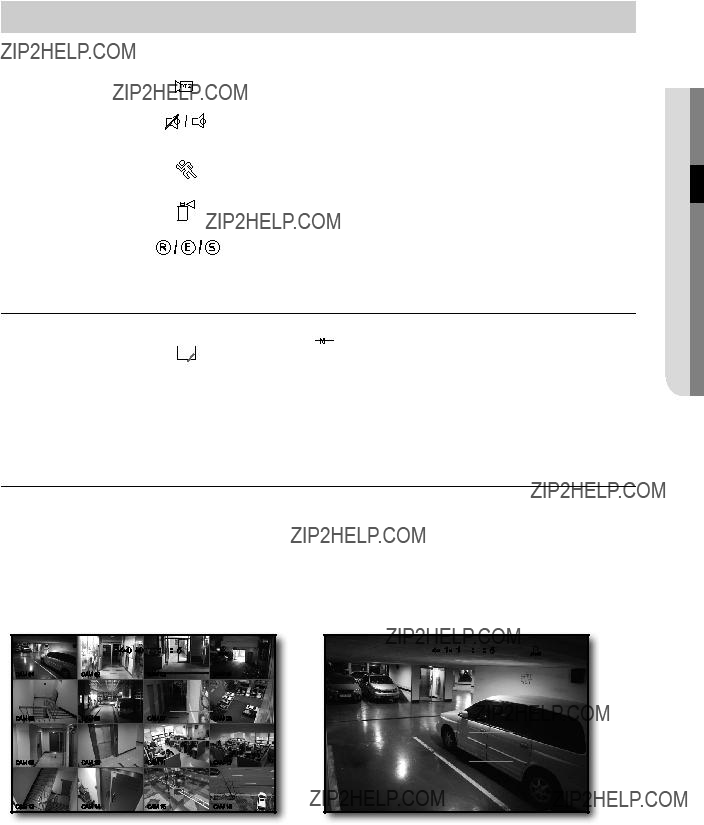
Live Screen Configuration
Icons on the Live Screen
You can check the status or operation of the DVR with the icons on the live screen.
Displayed when the
Displayed if a new firmware is found from the network.
This will be displayed if the backup operation is in process.
22_ live
error Information
???If the internal HDD is not connected, the ???NO HDD???( 

 ) message will appear; if there occurs a problem, you will see the ???HDD FAIL???(
) message will appear; if there occurs a problem, you will see the ???HDD FAIL???(  ) message in the top left corner. In this case, make sure you contact the service center for assistance as this may cause a failure of recording, playback or backup.
) message in the top left corner. In this case, make sure you contact the service center for assistance as this may cause a failure of recording, playback or backup.
M ` If you see NO HDD, HDD FAIL icons on the screen, contact the service center for more details.
Live Screen menu
In addition to the buttons on the remote control, you can access a desired menu by
The context sensitive menu that appears by
M ` Menu items of Search, Record, Backup and Shutdown can be deactivated, depending on the user permission.
< Split Mode Menu >< Single Mode Menu >
LIve!
English _23
live
Split mode menu
The context sensitive menu in split mode differs, depending on the login/logout status.
24_ live

Single mode menu
The single mode menu is available only in Single Mode.
The context sensitive menu for the One Channel mode, in Split mode is different from that of the Single mode.
LIve!
English _25

live
view the Launcher menu
The Launcher menu appears on the bottom of the live screen.
1.In Live mode,
2.Move the cursor to the bottom and click a desired item in the Launcher menu.
26_ live
Live Mode
Switching the screen mode
To switch the split mode, select a screen mode in the launcher menu, or
Press the [MODE] button on the remote control to switch the mode in the sequence of the launcher menu items.
MM``
Switching the split mode
Auto Sequence
live!
English _27
live
MM`` In Single mode, If you have set
`` In a split mode, If you have set <Multi CH SEQ Time> in ???Setting the Device > Monitor???, Auto Sequence will be conducted at the set interval. (Page 51)
Manual Switching
Press the left/right button on the remote control, or click the arrow <_/+> key to move to the next split mode.
???If pressing the right [+] button in
???If pressing the right [+] button in
Channel (CH 1~4) ??? Channel (CH 5~8) ??? Channel (CH 9~12) ??? Channel (CH 13~16) ??? Auto Sequence
28_ live

Channel Setting
Switching to Single Mode
When in split mode, select and
Press the number corresponding to a desired channel on the remote control to switch to its Single mode.
???CHANNEL
???CHANNEL 10 : Press the [0/+10] button.
???CHANNEL
`` Ex : If
English _29
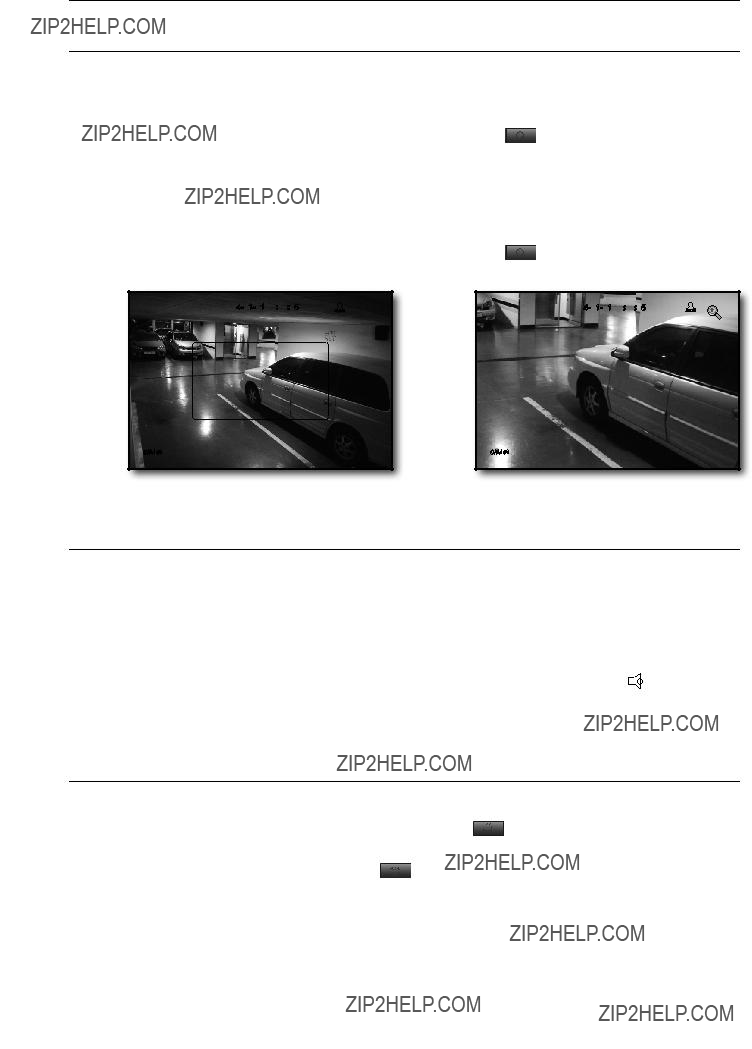
live
2.Use the direction keys, or drag and drop to specify an area to enlarge.
3.Press the [enTer] button, or
`In the enlarged image, use the direction buttons ($%_ +) on the remote control to move the enlarged area.
;
AudIo on/off
You can turn the sound on/off corresponding to the channel in Live mode.
AudIo on/off in Single mode
Click the audio icon (  ) on the screen, or press the [AudIo] button on the remote control to turn it on/off.
) on the screen, or press the [AudIo] button on the remote control to turn it on/off.
M ` Only the channel where <Audio> is set to <ON> in ???Device > Camera??? displays the audio icon ( ) in Live mode that you can use to turn the sound on/off.
freeZe
This is available only in Live mode, this pauses playing the Live image temporarily.
30_ live

Event Monitoring
This will display the channel in sync with a specific event (Motion/Tampering/Video Loss) if it occurs.
In ???Monitor > Event Display???, set the event monitoring to ON/OFF and specify the event display time. (Page 51)
Stop alarm
CH1
`` Ex : If you set <Event Display> to 5 seconds, and the second event occurs in CH 2 within the set time after the first event occurred in CH 1.
JJ`` In case of continuous events such as motion detection, switching to another split mode display may not immediate if concatenating events follow, even when you stopped alarm of the event.
English _31

main menu
You can setup the system properties, devices, and options for recording, event, backup and network.
SYSTEM SETUP
You can setup Date/Time/Language, Permission, System Properties and Log.
Date/Time/Language
You can check and setup the current Date/Time and time related properties, as well as the language used for the interface on the screen.
Setting the Date/Time/Language
Set the Date/Time/Language
Using the mouse may help make setup easier.
1.Press the [MENU] button on the remote control.
`If not logged in, it prompts with login window. Refer to ???Login???. (Page 21)
2.Use the left/right buttons (_ +) to select the <System>. System property setup menu is selected.
3.Use the up/down buttons (??????) to select <Date/Time/ Language> and press the [ENTER] button.
4.Select <Date/Time/Language>.
A dialog to setup Date, Time and Language.
5.Use direction buttons (??????_ +) to select an item to set and make your changes.
LogoutReturn
System
 Date/Time/Language
Date/Time/Language
Permission Management
 System Management
System Management
Log Information
32_ main menu

M ` You can also use numeric buttons on the remote control to enter values for Date, Time and other numeric fields.
MENU MAIN!
English _33

main menu
Setting Holiday
You can set specific dates to Holidays according to your preferences.
Holidays are applied to <Recording Schedule> and <Alarm Schedule> too.
Using the mouse may help make setup easier.
4.Use direction buttons (??????_ +) to select a desired date, and press the [ENTER] button.
You will see the ???Setting Holiday??? screen.
`Ex : Select January 8th and check on <1/8> only to make every January 8th a holiday. Check both on <1/8> and
<Jan 2nd Wed> to make every January 8th and 2nd Wednesday of January holidays.
5.When the Holiday setup is done, press <OK>.
Using the Calendar
Using the mouse may help make setup easier.
???Select year and month.
Select the left/right <
 > key on the left/right side of year/month and press [ENTER] button to adjust by 1 year/month.
> key on the left/right side of year/month and press [ENTER] button to adjust by 1 year/month.
???Use direction buttons to select a date and press [
`A date with recorded data to be searched will appear in yellow in the System Log, Event Log, Time Search and Event Search.ENTER
34_ main menu

Permission Management
You can set permissions of each user over the DVR's specific function and settings.
Setting the Administrator
You can set and change Administrator???s ID and password.
The administrator can use and set all menu items and functions.
Using the mouse may help make setup easier.
MENU MAIN!
1.Use the up/down buttons (??????) in <System> window to move to <Permission Management>, and press [ENTER] button.
2.Select <Admin>.
A dialog for Admin ID and Password input appears.
3.Use direction buttons (??????_ +) to move to a desired item, and set the ID and password.
Permission Management
OK Cancel
`Please change your password every three months to safely protect personal information and to prevent the damage of the information theft.
Please, take note that it???s a user???s responsibility for the security and any other problems caused by mismanaging a password.
4.When the administrator setup is done, press <OK>.
Using Virtual Keyboard
???For alphanumeric inputs, the virtual keyboard window appears.
???Use direction buttons (??????_ +) to move to a desired character, and press the [ENTER] button.
???In the upper text input box of the virtual keyboard, there displays a list of candidate words containing the selected character.
???Select a word from the list, or use the keyboard to enter the whole word.
`If there are many of candidate words, use <  ,
,  > buttons to move between them forward and backward.
> buttons to move between them forward and backward.
???Select <OK>.
Entered word is applied.
`For upper case letters, use <Caps Lock> button.
`For special characters, use <Shift> button.
`Using the virtual keyboard is the same to a normal keyboard use in your region.
`You can enter only
`For the password, use alphabets and special characters excluding < \ > and <???>.
`You can use number buttons on the remote control.
English _35

main menu
Setting the Group
You can create user groups and setup permissions for those user groups.
You can register a user for each group in <User>.
-Add : When you first run the DVR with the admin account, only the admin account exists. Add has already been deactivated. Select <Add> to display the virtual keyboard. Enter a group name. You can add up to 10 groups.
-Delete : Deletes a user group that is already registered. Selecting Delete will delete all user accounts belonging to that group.
-Rename : Renames a group that is already registered. Select <Rename> to display the virtual keyboard.
` For entering a group name, refer to ???Using Virtual Keyboard???. (Page 35)
???Group Authority : Sets permissions to access menu items of each group. Users of a group can access checked functions.
4. When the group setup is done, press <OK>.
To set the group authority
You can set the permissions of the group users to access the menu according to the channel.
1.Select a menu to which the group permission is assigned. The menu where the group permission is assigned will be displayed in the Live menu when a group user logs in.
???Live View : You can set the permission to access the Live screen according to the channel.
`
???Search : You can set the permission to access the Search menu according to the channel.
???Backup : You can set the permission to access the Backup menu according to the channel.
Permission Management
2.Select <OK>.
Select and assign a group user so that the user can access the specified menu.
36_ main menu

To restrict the user permissions
If the admin restricts all permissions of an added group, the users belonging to that group can access only the default minimum menus and can change the user???s own password only.
1.Start the DVR.
If all permissions are restricted, only the Login dialog should appear.
2.Log in with a registered user ID.
3.
If all permissions are restricted, only the accessible context menus should appear.
Login
Scene Mode ???
Audio Off
Freeze
Stop Alarm
Record
User Menu
Hide Launcher
Logout
MENU MAIN!
To change the user password
English _37

main menu
Setting the User
Users can be added only if a group was created in <Group> menu.
Using the mouse may help make setup easier.
1. Use the up/down buttons (??????) in <System> window to move to <Permission Management>, and press [ENTER] button.
2. Select <User>.
A window for Add User appears.
3. Use direction buttons (??????_ +) to select <Add> from the window.
A window for ???Add User??? appears.
You can configure the Network Viewer settings including name, ID, viewer, Select Group and password.
Result of the user setup appears in the <User> window. To change the user property, use ???Edit User???.
The ???Edit User??? window appears when you select a desired item to be changed in the <User> window.
??? Viewer : If you select <Use>, you will be given access to the Web Viewer and Network Viewer.
` Refer to ???Connecting Web Viewer???. (Page 82)
` For more information about use of SmartViewer, refer to the SmartViewer's user guide.
4. When the user setup is done, press <OK>.
Permission Management
38_ main menu

3. Use direction buttons (??????_ +) to move to a desired item, and set the value.
??? Restricted Access : All menu items allowed for a user can be set with restricted access.
- Checked ( 

 ) : Restricted
) : Restricted
- All Network : Restricts all access instances via Network Viewer and Web Viewer.
- Web Viewer : Restricts access via the Web Viewer.
MENU MAIN!
English _39
main menu
System Management
You can check the system version, update to a newer version, as well as data backup and initialization.
Checking the System Information
You can check the current system version, broadcasting system, MAC address. You can update the system.
4. When the recognized device appears, select <Upgrade>.
` The <Upgrade> button will be activated only if the current <Software Version> of the <System Information> is same to or older than that of <S/W Upgrade>.
5.Press <OK> in the ???System Upgrade??? window.
`While updating, it shows the progress.
System Management
Previous
40_ main menu

6.When the updating is done, it automatically restarts. Do not turn the power off until it finishes restarting.
MENU MAIN!
English _41
main menu
Settings
???Storage Device : Shows the connected storage device.
???DVR???USB : Exports DVR settings to the connected storage device.
???USB???DVR : Imports DVR settings from the storage device and applies to the DVR.
` If <Include Network Settings> is checked, the network settings will be imported too.
`After importing the configuration, please reboot DVR to take effect.
???Load Factory Default : If <Default> is selected, a confirmation dialog for ???Load Factory Default??? prompts. Press <OK> to initialize the system to the factory default.
`DVR will restart after loading facotry default.
4. To move to the previous menu, press <Previous>.
System Management
Previous
Log Information
You can browse logs on the system and events.
System Log
System Log shows log and timestamp on every system start up, system shutdown, and changes on system settings.
3. Use direction buttons (??????_ +) to move to a desired item, and press <Search>.
42_ main menu
Event Log
Event log shows recorded events on alarms, motion detections and video loss.
It also shows the log and its timestamp.
Using the mouse may help make setup easier.
Backup Log
You can find out who backed up and the details (backup time, channel, device to use, file format, etc.). Using the mouse may help make setup easier.
menu main!
English _43

main menu
SETTING THE DEVICE
You can configure the settings of: Camera, Storage Device, Remote Device and Monitor.
Camera
Setting the Camera
You can set Video, Audio, Channel Name and Dwell Time of a Camera. Using the mouse may help make setup easier.
1.Press the [MENU] button on the remote control.
2.Use the left/right button (_ +) to select <Device>. Device setting menu is selected.
3.Use the up/down buttons (??????) to move to <Camera>, and press [ENTER] button.
LogoutReturn
`For privacy protection, it does not display the video while the recording continues.
-<Covert2> : Shows nothing but an empty screen while the recording continues.
???Audio
-If set to <ON>, you can turn the audio of the channel ON on the Live screen.
-If set to <OFF>, the channel???s audio is off on the Live screen and not recorded.
`Audio output is available for only 1 channel.
`
???CH Name : Up to 15 characters including blanks are allowed.
` Refer to ???Using Virtual Keyboard???. (Page 35)
???
` If set to <OFF>, the channel is not listed in the Auto Sequence mode.
???Type : You may setup the numbers of HD channel based on your needs, after completing setup, please click OK on HD/SD Switch menu, and DVR would restart to take effect.
44_ main menu

???Screen Setup : The video appeared on the screen may vary depending on the channel???s camera, configure the DVR display to your preferences.
Select a channel and adjust the <

 (Brightness)>,
(Brightness)>,
<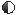 (Contrast)>, and <
(Contrast)>, and < (Color)> of the selected channel.
(Color)> of the selected channel.
` Press the <Init> to initialize settings back to the default.
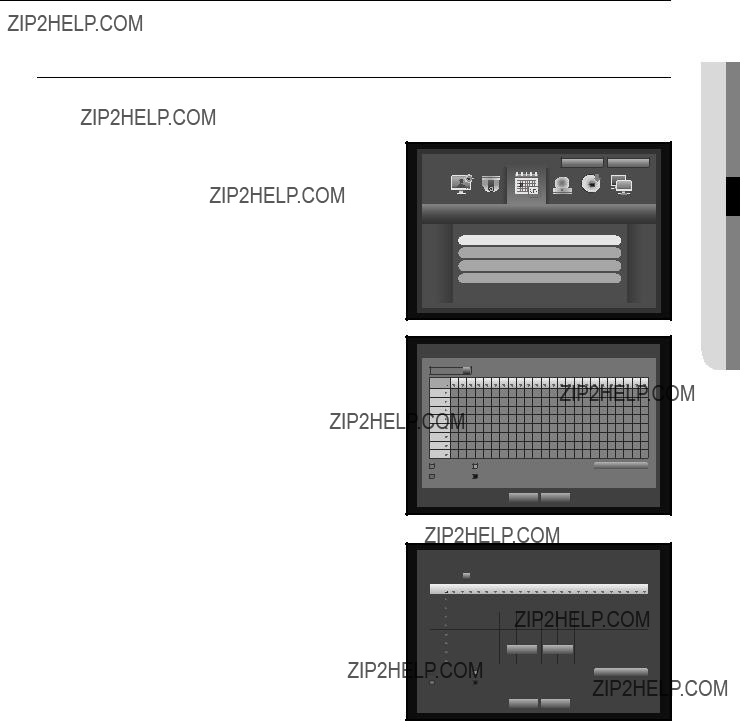
???Privacy Region : You can specify a certain area of the camera video to be protected for your privacy.
6. When the camera setup is done, press <OK>.
Screen Setup
MENU MAIN!
To set the privacy region
??? Select <Privacy Region>.
??? When ???Privacy Region??? window appears, select a channel for detection and set the area of motion detection.
??? To set the area in ???Privacy Region??? window
??? Privacy Region
You can specify up to 4 privacy zones for each channel, which can be identified by the color.
1  Purple 2
Purple 2  Green 3
Green 3  Blue 4
Blue 4  Yellow
Yellow
Privacy Region
CH1
Privacy Region1
OK Cancel
??? To set the area using <Individual> selection
When selected <Individual>, ???Privacy Region??? window disappears and you can select cells one by one. When the motion area setup is done,
- Clear All : Selected cell is removed from the Privacy Region.
- Menu : After selecting individual motion areas, move to the ???Privacy Region??? window.
` If selected <Apply to All CH>, selected motion area is applied to all channels.
??? When completing the privacy zone settings, click <OK>.
English _45

main menu
Setting the PTZ
To use Camera???s PTZ functions, ID and protocols of each camera and DVR should be matched. For other settings, refer to the <Remote Device> settings. (Page 50)
Using the mouse may help make setup easier.
???ID : Set the ID of the connected camera of each channel.
You can easily setup by using the numeric buttons on the remote control.
???Protocol : Set the protocol of the connected camera of each channel.
MM`` You can check the camera???s ID and protocol if you turn the camera off and on after connecting it to the DVR. `` For the <Coaxial> type, Only
4. When the PTZ setup is done, press <OK>.
46_ main menu

Storage Device
You can check information on storage devices.
Confirming Devices
You can check storage devices and their free space, usage as well as status.
Devices available are HDD, and USB devices (Memory, HDD).
Using the mouse may help make setup easier.
???Used/Total : Shows the used/total capacity of the storage device.
???Usage : Sets the storage device???s usage.
`` External USB HDD, SATA HDD are used for extension and backup.
`` A maximum of 2TB for each port is supported for backup on a high capacity SATA HDD such as RAID equipment.
`` If an eSATA HDD device is used for extended storage or backup purposes, disconnecting eSATA device may restart the system.
For backup use, the device can be disconnected if it???s not in use.
???Status/Management : Shows the current status of the HDD, as in Normal/Check/Replace.
3. To move to the previous menu, press <OK>.
menu main!
English _47

main menu
Formatting
You can format a storage device.
Using the mouse may help make setup easier.
1.Use the up/down buttons (??????) in <Device> window to move to <Storage Device>, and press [ENTER] button.
2.Select <Format>.
A window for selection of device for formatting appears.
3.Use direction buttons (??????_ +) to select a device to be formatted.
 Storage Device
Storage Device
Format
OK Cancel
4.Select <Format> on the bottom of the screen.
Press <OK> on the ???Manage??? confirmation window will start formatting the selected device.
5.When the formatting is done, press <OK>.
 Storage Device
Storage Device
48_ main menu

HDD Alarm
You can set alarm settings for HDD defects such as Check Alarm Output Port, Replace Alarm Output Port, and its duration.
Using the mouse may help make setup easier.
1.Use the up/down buttons (??????) in <Device> window to move to <Storage Device>, and press [ENTER] button.
2.Select <HDD Alarm>.
A window for setting HDD check and replace output ports and their durations appears.
3.Use direction buttons (??????_ +) to move to the desired item.
???Check Alarm Output Port : If HDD generates check alarm, the alarm signal will output to the specified alarm output port.
 Storage Device
Storage Device
menu main!
???Replace Alarm Output Port : If HDD generates replace alarm, the alarm signal will output to the specified alarm output port.
???Duration : Sets the alarm duration for the alarm signal and beep sound.
MM`` <Check> status means that the HDD is operating but it has problems that require technical examination. ( 

 ) appears on the Live screen.
) appears on the Live screen.
`` <Replace> status means that the HDD has defect and requires immediate replacement. ( 

 ) appears on the Live screen.
) appears on the Live screen.
`` If the installed HDD is not recognized properly, a confirmation popup will appear.
4. When the HDD Alarm setup is done, press <OK>.
English _49

main menu
Remote Devices
You can set the
Using the mouse may help make setup easier.
1.Use the up/down buttons (??????) in <Device> window to move to <Remote Device>, and press [ENTER] button.
2.Use direction buttons (??????_ +) to move to the desired item, and press [ENTER] button.
3.Set the values of each communication setup of the remote device.
???Baudrate : Baud rate settings of the DVR, PTZ camera should be matched for proper operations.
4.Make sure to match IDs of the DVR and Remote Control, and press <OK>.
Remote Device
OK Cancel
MM`` For changing the remote control???s ID, refer to ???Changing the Remote Control ID???. (Page 13)
50_ main menu

Monitor
You can configure information to be displayed and its format for Spot Out monitor.
Setting the Monitor
Using the mouse may help make setup easier.
???Display : Displays only checked items on the monitor screen.
???Multi CH SEQ Time : Sets the interval between automatic display switching in
???VGA/HDMI : Set your preferred screen resolution to <VGA> or <HDMI>.
If the monitor does not support selected resolution of <VGA> or <HDMI>, it may not display video properly.
???HDMI Resolution Auto Detection: If the option is checked on and the HDMI is available, DVR will automatically adjust optimized resolution based on monitor's setting. If you need to configure the resolution manually, please turn the option off.
4. When the monitor setup is done, press <OK>.
Screen Setup
menu main!
English _51

main menu
Setting the Screen Mode
You can configure the Live screen and Split Screens.
Using the mouse may help make setup easier.
1.Use the up/down buttons (??????) in <Device> window to move to <Monitor>, and press [ENTER] button.
2.Select <Mode>.
3.Use direction buttons (??????_ +) to move to a desired item, and set the value.
???Live Screen : Select split modes for the Live screen.
???Play Screen : Select split modes for the playback screen. Only the
Black shows the playback while white shows the Live screen.
4. When the screen mode setup is done, press <OK>.
 Monitor
Monitor
52_ main menu
Setting the Recording
You can setup scheduled recording, event recording and other recording related settings.
Recording Schedule
Make your reservation on a date and time to schedule the recording on specified time.
Using the mouse may help make setup easier.
menu main!
1.Press the [MENU] button on the remote control.
2.Use the left/right button (_ +) to select <Record>. Record menu is selected.
3.Use the up/down buttons (??????) to move to <Recording Schedule>, and press [ENTER] button.
LogoutReturn
Record
 Recording Schedule
Recording Schedule
 Event Record Duration
Event Record Duration
 REC Quality & Resolution
REC Quality & Resolution
 Record Option
Record Option
4.Select <Recording Schedule>.
A window of scheduled recording setup appears.
5.Use direction buttons (??????_ +) to move to a desired item, and set the value.
???Channel : Select a channel to set the recording schedule time and date format.
???Recording type : Select each time cell, and then select a type to start recording.
???Apply to All CH : If selected <Apply to All CH>, ???Apply to All CH??? window appears.
Press <OK> to apply the setup to all channels.
6. When the recording schedule setup is done, press <OK>.
MM`` Event recording and scheduled recording starts about 3 seconds prior to the event/schedule for guaranteed recording.
 Recording Schedule
Recording Schedule
English _53

Each press of a selected cell will cycle through <No
Event Record Duration
You can set the beginning and ending point of a recording on an event.
3. When the event recording duration setup is done, press <OK>.
REC Quality / Resolution
You can set resolution, FPS, and quality of recordings by channel, and by recording type of standard / event.
For more information about the resolution, refer to the ???Product Specification??? section. (Page 114)
Setting Standard Recording Properties
You can set each channel???s resolution, quality and FPS for normal recordings.
Using the mouse may help make setup easier.
1.Use the up/down buttons (??????) in <Record> window to move to <REC Quality & Resolution>, and press [ENTER] button.
2.Select <Standard>.
3.When the recording setup is done, press <OK>.
 REC Quality & Resolution
REC Quality & Resolution

 Previous/Next Page
Previous/Next Page
OK Cancel
54_ main menu

Setting Event Recording Properties
You can set each channel???s resolution, quality and FPS for event recordings.
Using the mouse may help make setup easier.
1.Use the up/down buttons (??????) in <Record> window to move to <REC Quality & Resolution>, and press [ENTER] button.
2.Select <Event>.
Event recording setup window appears.
3.Use direction buttons (??????_ +) to move to a desired item, and select it.
???Resolution : Sets the resolution of the recorded screen.
???Record Rate : Image Per Second, means the frames recorded per a second.
???Record Quality : Sets the recording quality.
 REC Quality & Resolution
REC Quality & Resolution
menu main!
MM`` You cannot increase the remaining count if the current remaining count has reached zero or there is no available remaining count from any other page. If this is the case, reduce the remaining count for the current page, or do so for the same channel on any other page.
4. When the Event recording setup is done, press <OK>.
Record Option
You can set the recording to stop or overwrite when the HDD is full.
Using the mouse may help make setup easier.
1. Use the up/down buttons (??????) in <Record> window to move to <Record Option>, and press [ENTER] button.
2. Use direction buttons (??????_ +) to move to a desired item, and set the value.
??? Disk End Mode : If selected <Overwrite>, recording will continue despite the HDD full while overwriting the oldest. If selected <Stop>, the recording will stop when the HDD is full.
??? Disk End Beep : If selected <Stop>, the button is activated. If you check it, the beep will sound on the disk full and the recording stops.
Record Option
???Auto Delete : If you check it, Record Period setup is activated.
If you specify the auto deletion period, the recording data before the period will be deleted automatically.
`` This option will be enabled only if Disk End Mode is set to <Overwrite>.
???HDD Free Space : Shows remaining free space available on the HDD.
???Recordable (days/hours) : Shows estimation of remaining days and hours for recording, based on the remaining free space.
3. When the recording option setup is done, press <OK>.
English _55
main menu
SETTING THE EVENT
You can set recording options when motion, image loss detection or tampering event occurs.
Motion Detection
You can set target detection region and motion, as well as the alarm signal output.
When the motion detection region is set, it detects motion within the area.
??? Alarm Duration : Sets the duration of alarm signal and alarm sound. 5. When the motion detection setup is done, press <OK>.
Setting the Motion Detection Area
??? Select <Motion Region>.
??? When ???Motion Region??? window appears, select a channel for detection and set the area of motion detection.
??? To set the area using <Individual> selection
In the ???Motion Region??? window, you can select cells individually by using <Individual>.
Motion Region
CH1
OK Cancel
When selected <Individual>, ???Motion Region??? window disappears and you can select cells one by one.When the motion area setup is done, press the <Menu> on the screen or the [MENU] button on the remote control to display the ???Motion Region??? window again.
-Select : Selected cell is set to be a part of motion detection area.
-Unselect : Selected cell is removed from the motion detection area.
-Inverse : Unselected cells are set to be the motion detection area.
-Menu : After selecting individual motion areas, move to the ???Motion Region??? window.
` If selected <Apply to All CH>, selected motion area is applied to all channels.
???When the motion detection setup is done, press <OK>.
 Select
Select
Unselect
Inverse
Menu
56_ main menu

Video Loss Detection
You can set the alarm to be generated on a camera disconnection, which causes a video loss.
Tampering Detection
You can set to detect tampering attempts and trigger events, such as sudden change of camera???s framing direction, blocked lens and other overall change of scenes from the video.
Using the mouse may help make setup easier.
menu main!
1.Use the up/down buttons (??????) in <Event> window to move to <Tampering Detection>, and press [ENTER] button.
Tampering detection settings screen appears.
2.Use direction buttons (??????_ +) to move to a desired item, and set the value.
???Mode : Set whether to use Tampering Detection or not.
???Sensitivity : Set the sensitivity level of tampering detection.
???Alarm : Set the alarm output method.
???Duration : Set the alarm signal output and its dwell time.
3. When the tampering detection setup is done, press <OK>.
Tampering Detection
MM`` Since the tampering detection is designed and optimized to function in accordance with the user defined sensitivity level, it may not render a significant difference in detection with varied sensitivity in general monitoring situations.
`` When the tampering detection mode is set <ON>, it is recommended that the pre event recording time of the corresponding channel should be set to 10 seconds or longer.
English _57
main menu
Alarm Schedule
You can set the conditions and operating hours for scheduled alarms.
Using the mouse may help make setup easier.
1. Use the up/down buttons (??????) in <Event> window to move to <Alarm Schedule>, and press [ENTER] button.
???OFF : Marked in white, no alarm is generated even if an event occurs.
???Event Sync : Marked in Blue, generates alarm only when an event occurs.
MM`` When the alarm is generated on the scheduled time, you can stop the alarm by canceling the schedule.
3. When the Alarm Schedule setup is done, press <OK>.
Backup
You can check the backup device and set the backup schedule by channel or by time. The product only supports external HDD of USB memory and USB/SATA type. (Page 114)
Setting the Backup
You can backup the desired data to a connected device.
Using the mouse may help make setup easier.
1.Press the [MENU] button on the remote control.
2.Use the left/right button (_ +) to select <Backup>. Backup menu is selected.
LogoutReturn
Backup
 Backup
Backup
58_ main menu

3. Press the [ENTER] button. A backup window appears.
You can directly access it from the ???Live screen menu???. (Page 23)
4. Use direction buttons (??????_ +) to move to a desired item, and set the value.
??? Backup Range : Sets the <Start> and <End> time for the backup.
??? Channel : Sets the channel to backup. You can select multiple channels.
 Backup
Backup
menu main!
???Device : Select a backup device from the recognized devices.
???Type : Sets the backup data format.
`` If you need to install a codec in Windows, run the x264_dvr.exe file in the codec folder that is created when you back up an AVI file.
???File Name : You can set the back file name.
`` Refer to ???Using Virtual Keyboard???. (Page 35)
???Check capacity : Shows the size of the selected backup data, used and available capacity of the selected backup device.
???Overlap : Shows a list of overlapping data on a same time according to the number of data.
It appears when one channel has multiple data on a certain time point due to changing of time or time zone settings, etc.
`` Refer to time and time zone of ???Setting the Date/Time/Language???. (Page 32)
5. When the backup setup is done, press <OK>.
`` If no available device is recognized for backup, <OK> button is not activated.
JJ`` The application may slow down during the backup.
`` You can switch to the menu screen during the backup in operation, but playback of data is not available. `` The data can be played back on a Webviewer while the backup is in progress but audio does not function.
`` When a memory device is used for backup, it is not available to use the full capacity of the media since the system consumes a part of its capacity.
`` If backup has failed, select ???Device > Storage Device??? and check the free space of the HDD and check also if the HDD is properly connected.
MM`` Pressing the <Exit> during the backup will return to the previous menu, while the backup progresses.
English _59

main menu
Network Configuration
It provides networked monitoring of Live screen from a remote place, and supports mail forwarding function with events. You can configure the network environment which enables such functions.
Please refer to the Quick Guide enclosed when connecting a network with the wireless USB adaptor used only for Samsung DVR.
Connection Mode
You can set the network connection route and protocol.
Setting the Connection
Sets the protocol and environment of the network.
Using the mouse may help make setup easier.
1.Press the [MENU] button on the remote control.
2.Use the left/right button (_ +) to select <Network>. Network menu is selected.
3.Use the up/down buttons (??????) to move to <Connection Mode>, and press [ENTER] button.
LogoutReturn
Network
 Connection Mode
Connection Mode
 DDNS
DDNS
 Live Transfer
Live Transfer
 Mailing Service
Mailing Service
4.Select <Interface>.
A window of connection mode setup appears.
5.Use direction buttons (??????_ +) to move to a desired item, and set the value.
???IP Type : Sets the network connection mode.
???Transfer Bandwidth : Sets the maximum data flow to be transferred. (Upload speed)
Options will vary depending on the selected connection mode.
???IP Address, Gateway, Subnet Mask, and DNS
???ID, Password : In case you selected PPPoE, provide the ???ID??? and its ???Password???.
MM`` DNS server for <DHCP> and <PPPoE> can be set by user only if you selected <Manual>.
6. When the connection setup is done, press <OK>.
60_ main menu

`` If selected UDP, selections of Device Port, UDP Port and Unicast/Multicast are activated.
`` If setting the connection mode to PPPoE, you cannot select UDP for the protocol type.
??? Device Port : Initially, <4520~4524> is set. It increases / decreases by 5.
??? UDP Port : Initially, <8000~8160> is set. It increases / decreases by 160.
??? Unicast/Multicast : Select one between
??? Multicast IP Address : User can directly input.
??? Multicast TTL : Select from 0 ~ 255. Initial value for the TTL is set to <5>.
??? HTTP Port : Enter the port number for the Web Viewer. Initially, it is set to <80>.
??? Multi Browser Support : The Web Viewer can be used with a browser that supports the Silverlight.
The multi viewer can be used only if the HTTP port is set to 80, protocol type is TCP and device ports range within
This is for the Siliverlight???s security purposes.
??? Secure Video Transmission: Determine the network video transmission data is encrypted or not. Encrypt: ON, Not Encrypt: OFF.
If you set the secure video transmission mode, the max bandwidth performance will be limited. When ON is selected, multi browser is not supported.
4. When the protocol setup is done, press <OK>.
English _61
























































Samsung Techwin respeta el medio ambiente durante todo el proceso de fabricaci??n de sus productos y realiza una serie de procedimientos orientados a ofrecer productos ecol??gicos.
El s??mbolo Eco representa el compromiso de Samsung Techwin de fabricar productos que respeten el medio ambiente e indica a la vez que este equipo cumple con la Directiva de la Uni??n Europea EU RoHS.
Correct Disposal of This Product (Waste Electrical & Electronic Equipment)
(Applicable in the European Union and other European countries with separate collection systems)
This marking on the product, accessories or literature indicates that the product and its electronic accessories (e.g. charger, headset, USB cable) should not be disposed of with other household waste at the end of their working life. To prevent possible harm to the environment or human health from uncontrolled waste disposal, please separate these items from other types of waste and recycle them responsibly to promote the sustainable reuse of material resources.
Household users should contact either the retailer where they purchased this product, or their local government office, for details of where and how they can take these items for environmentally safe recycling.
Business users should contact their supplier and check the terms and conditions of the purchase contract. This product and its electronic accessories should not be mixed with other commercial wastes for disposal.
Correct disposal of batteries in this product
(Applicable in the European Union and other European countries with separate battery return systems.)
This marking on the battery, manual or packaging indicates that the batteries in this product should not be disposed of with other household waste at the end of their working life. Where marked, the chemical symbols Hg, Cd or Pb indicate that the battery contains mercury, cadmium or lead above the reference levels in EC Directive 2006/66. If batteries are not properly disposed of, these substances can cause harm to human health or the environment.
To protect natural resources and to promote material reuse, please separate batteries from other types of waste and recycle them through your local, free battery return system.

SALES NETWORK
SAMSUNG TECHWIN CO., LTD.
6,
www.samsungsecurity.com