7.4CUSTOMER RESPONSIBILITY
As shown above, the SNMP/Web adapters implement advanced security features. Nevertheless, achieving complete security protection requires the introduction of a comprehensive security program. This section lists some good practices in network security that customers are recommended to adopt.
7.4.1 Physical security
Most of the security features would prove useless if physical access to the equipment is uncontrolled. In fact, physical access is probably the major security hazard for a site.
This problem may be efficiently tackled by installing the equipment in a secure area and by implementing access control policies.
7.4.2 Changing default configuration
It is recommended that users change the adapter default configuration at their very first access. Particularly, it is recommended to focus on the following settings:
???The default username and password for the superuser are ge and ge. It is recommended to change default username and password (by configuring new and unique ones) at the initial card configuration
???Any service is associated with a specific port. The default configuration uses the standard port for each protocol (e.g. 161 for SNMP). If the user specifies a non-standard port for a service this increases security by hiding the relevant interface to malicious users.
???Further to this, SNMP access is controlled by read and set community settings. These respectively default to public and private. Once again, changing these settings may help in increasing security.
It is clear that username, password and service configuration must remain secret in order to provide an efficient security protection. If this information becomes public the entire authentication method loses effectiveness.
7.4.3 User & Service management
As shown above, the SNMP/Web adapters offer advanced user management features, by offering different access rights and allowing selective activation of services.
It must be noted that every running service exposes the system to a possible attack. Minimising the number of running services may increase overall protection. It is therefore recommended to disable unused services.
7.4.4 Encryption
In most network protocols, sensitive information (e.g. username/password pairs) is transmitted over the network as plain text. This may not be a problem in most installations, but it may become critical when malicious users can gain access to the network traffic.
The introduction of encryption provides and higher degree of security by ensuring that exchanged data cannot be intercepted. The SNMP/Web adapters provide an encryption-protected alternative for the main access methods:
???Web interface: use HTTPS (SSL ??? Secure Socket Layer) protocol
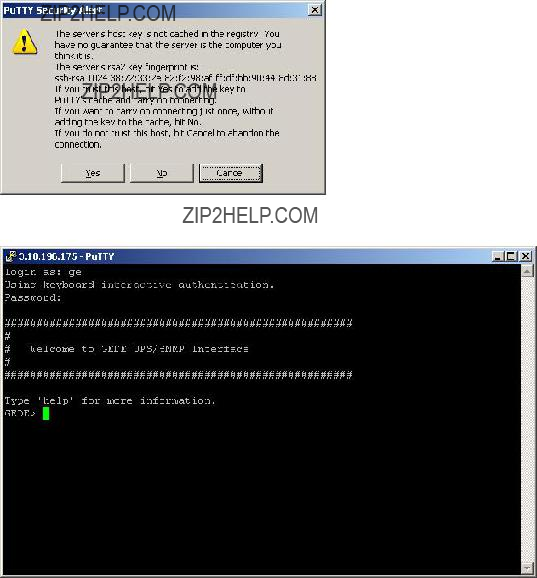
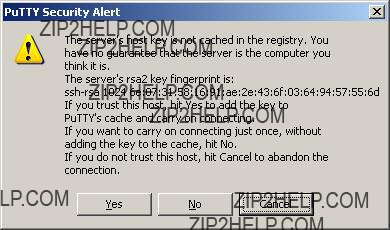
???Remote console interface: use SSH (Secure Shell) protocol
???File transfer: use SFTP (Secure FTP)
7.4.5 Firewalls
It should be now clear that although some protocols and some access methods might provide a higher degree of security, every customer is encouraged to implement a comprehensive security scheme, of which the SNMP/Web adapters are only a single node.
The partition of the network in sub-networks and the introduction of firewalls with stringent rules are a critical component in the global security program.


 UPS
UPS